Although short-term strategies and rapid trades are prevalent in the crypto market, best long-term crypto investments in cryptocurrencies offer the potential for substantial returns. The market currently boasts nearly 23,000 crypto projects available for investment.
In this article, we present the best 9 long-term crypto investing. Also, we provide you with a list of pros and cons of investing and give some tips and tricks to make the investment process smoother. You can find the FAQ section here, too.
The crypto projects we suggest for your investment:
- Bitcoin (BTC)
- Ripple (XRP)
- Avalanche (AVAX)
- Solana (SOL)
- Cardano (ADA)
- Ethereum (ETH)
- Binance Coin (BNB)
Key Information
Here, you can find main information about our selected projects:
🪙 Bitcoin (BTC) maintains its position as the foremost cryptocurrency in , characterized by its widespread adoption, clear use case, and unmatched security and transparency.
🪙 XRP, on the Ripple blockchain, surged by 6,000% from 2017 to May 2023, trading at around $0.53 with a market cap of $27 billion as of June 13, 2023, amid a significant legal dispute with the SEC, while offering various trading pairs.
🪙 Avalanche (AVAX), an essential token in the ecosystem, is positioned for long-term success with ambitious goals set by the Avalanche blockchain and a dedicated team behind it, envisioning a future where businesses and individuals establish their blockchains through subnetworks.
🪙 Solana (SOL) is a blockchain designed for high-speed, high-volume transactions, offering scalability and efficiency. Despite some concerns about tokenomics and security, it presents substantial potential for growth and adoption, particularly if it addresses technical hurdles and usability issues.

🪙 Cardano (ADA) is a blockchain platform that provides a more efficient, sustainable, and interoperable environment for smart contracts and decentralized applications. It addresses scalability, interoperability, and sustainability issues in blockchain technology.
🪙 Ethereum (ETH) is a highly influential blockchain platform for introducing smart contracts and decentralized applications. Despite ongoing discussions about its long-term position, it boasts significant market capitalization, liquidity, and adoption, making it a crucial asset for best long-term crypto portfolio.
🪙 Binance Coin (BNB) is the largest cryptocurrency associated with a cryptocurrency exchange, with high market capitalization, liquidity, and trading volume. While it offers numerous use cases and benefits from a strong community, concerns about centralization and potential regulatory risks should be considered in investment decisions.
Long Term Crypto Projects
Here, we will take a closer look at each best crypto to invest for long term:
Bitcoin (BTC)
Bitcoin (BTC) remains the leading cryptocurrency in, boasting high market capitalization, trading volume, and liquidity. Its adoption and use case is widespread, making it a portfolio staple.
While its tokenomics indicate negligible inflation and a capped supply, the development team and community support are robust. Bitcoin’s security and transparency are unmatched, functioning closest to actual currency.
However, due to its significant market cap, the era of rapid, high-risk gains may be waning, making it potentially unsuitable for those seeking such outcomes..
Ripple (XRP)
The Ripple blockchain network facilitates the exchange of cryptocurrencies and traditional fiat currencies. From 2017 to May 2023, XRP’s value surged by approximately 6,000%, establishing it as one of the most promising best long-term investment cryptocurrency.
As of June 13, 2023, XRP is trading at nearly $0.53, and its total market capitalization is around $27 billion.
A legal dispute involving the SEC was launched against Ripple in 2020. There is an expectation that this lawsuit will conclude soon, and stakeholders are eagerly awaiting the outcome, anticipating its potential impact on the price of XRP.
Avalanche (AVAX)
The AVAX token, an integral part of the Avalanche ecosystem, secures its position on this roster due to the ambitious objectives set forth by the Avalanche blockchain and the committed team driving those aspirations.
Ava Labs, the brains behind Avalanche, envisions a future where most businesses and even numerous individuals will seek to establish their blockchains. Consequently, Avalanche enables individuals to utilize subnetworks to deploy their miniature blockchains atop its platform.
The vision outlined by Ava Labs has already piqued the interest of numerous individuals and corporations. Should Avalanche achieve widespread adoption, AVAX stands poised to emerge as a solid, long-term success.
Solana (SOL)
Solana (SOL) is engineered for rapid, high-capacity transactions, excelling in various use cases with swift adoption.
While its tokenomics exhibit moderate characteristics, challenges remain in Solana’s unique consensus algorithm. Security concerns arise from high resource costs, potentially centralizing network control.
Performance is commendable, but its association with Sam Bankman-Fried has impacted its reputation. Overcoming technical hurdles and delivering on usability promises could see SOL rebound significantly, though it involves higher risk and reward than other leading projects.
Cardano (ADA)
Cardano (ADA) is a high-cap cryptocurrency fostering efficient, eco-friendly smart contracts and dApps. While it boasts a substantial market cap and widespread use cases, concerns arise from initial supply concentration.
The project prioritizes security and transparency, though vigilance against malicious smart contracts is advised. Despite a deliberate research-driven development, Cardano faces both strong support and opposition, offering a potentially robust yet polarizing investment opportunity.
Ethereum (ETH)
Ethereum (ETH) has played a key role in the rise of smart contracts and decentralized apps, with a solid market cap, high trading volume, and strong liquidity. It’s widely adopted and backed by a solid development team and community support.
When it comes to trading strategies, Ethereum offers opportunities due to its substantial use case and strong market dynamics. While its security and transparency are top-notch, it’s important to be cautious about risky smart contracts. Ethereum’s deflationary model, introduced after the merge, helps maintain its strong performance.
Even though Ethereum is well-established, some still debate its long-term potential, making it a valuable yet evolving asset in any crypto portfolio.
Binance Coin (BNB)
Binance Coin (BNB) is the foremost cryptocurrency associated with a crypto exchange. It exhibits high market capitalization, trading volume, and liquidity, with a significant user base.
While its tokenomics include a burn mechanism to reduce supply, there’s concern about a concentration of supply in the hands of founders and early investors, potentially influencing the market. BNB benefits from a strong development team and community support.
However, security and transparency are flagged as areas of concern, as Binance Smart Chain and related entities are controlled by a small group, posing potential risks.
BNB’s versatility is expanding, offering various use cases, but its centralized foundation raises regulatory and fraud-related risks, necessitating trust in investment decisions.
Pros and Cons of Long-term Crypto Investment
Before making decisions on best longterm crypto investment, consider the pros and cons:
Pros
Potential for High Returns: Historically, cryptocurrencies have shown the potential for significant price appreciation over time. Early adopters of Bitcoin, for example, have seen substantial gains.
Diversification: Adding cryptocurrencies to an investment portfolio can provide diversification, as their price movements often do not correlate with traditional asset classes like stocks and bonds.
Accessibility: Cryptocurrencies can be easily bought and stored online, making them accessible to a global audience. This accessibility democratizes investment opportunities.
Innovation and Technology: Investing in cryptocurrencies allows individuals to support and be part of innovative blockchain technologies and decentralized applications that have the potential to revolutionize various industries.
Global Reach and Inclusivity: Cryptocurrencies can provide financial services to individuals who may not have access to traditional banking systems, particularly in regions with limited infrastructure.
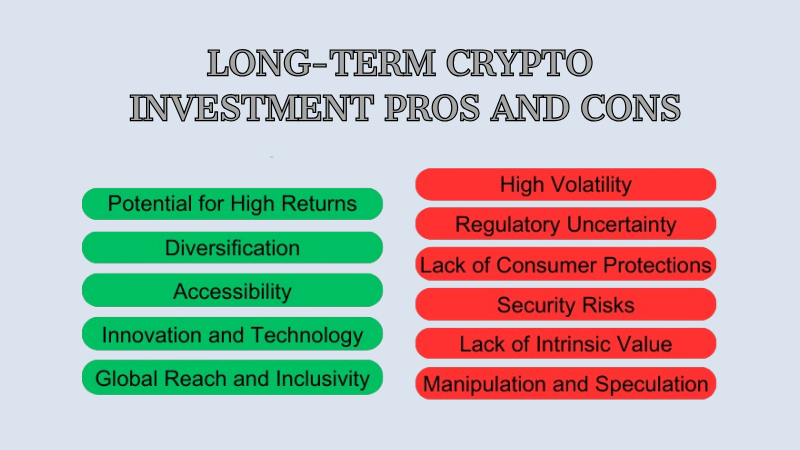
Cons
High Volatility: Cryptocurrencies are known for their extreme price volatility. While this can lead to significant gains, it also exposes investors to higher levels of risk.
Regulatory Uncertainty: The regulatory landscape for cryptocurrencies is still evolving. Changes in regulations can impact the value and legality of certain cryptocurrencies.
Lack of Consumer Protections: Unlike traditional financial systems, cryptocurrency transactions are irreversible. If a mistake is made, there may be no recourse to recover lost funds.
Security Risks: Storing cryptocurrencies requires secure practices. If a wallet or exchange is compromised, it can lead to loss of funds. This risk can be mitigated with proper security measures.
Lack of Intrinsic Value: Unlike assets like stocks or real estate, cryptocurrencies do not have underlying assets or cash flows. Their value is largely determined by market demand.
Market Manipulation and Speculation: The cryptocurrency market can be influenced by speculative trading, pump-and-dump schemes, and other forms of market manipulation.
Investors must conduct thorough research, understand risk tolerance, and consider their overall long-term crypto investment strategy before investing in long-term crypto investments.
Diversification and a long-term perspective can help mitigate some of the risks associated with the cryptocurrency market.
Insights About Best Long-Term Crypto Projects
Here are some knowledge and insights for crypto to buy for long-term investment:
💡 Understand the Technology: Gain a basic understanding of blockchain technology and how the specific cryptocurrency you’re interested in operates. This will help you make informed decisions.
💡 Diversify Your Portfolio: Avoid putting all your funds into a single cryptocurrency. Diversification can help spread risk and increase the potential for long-term gains.
💡 Choose Established Projects: Consider investing in well-established cryptocurrencies with a track record of stability and adoption. These are generally considered safer bets for best crypto for long-term investment.
💡 Stay Informed: Keep up with best cryptocurrency long-term news, updates, and trends. This helps you stay aware of any developments that could impact your investments.
💡 Use Secure Wallets: If you’re holding cryptocurrencies long-term, consider using hardware wallets or other secure cold storage options. This reduces the risk of hacks or theft.
💡 Ignore Short-term Price Fluctuations: Don’t get overly concerned with day-to-day price movements. Best crypto long-term investment is about the overall growth trajectory over an extended period.
💡 Beware of Scams and Frauds: Be cautious of phishing attempts, fraudulent projects, and Ponzi schemes. Verify information from official sources and be skeptical of unsolicited offers.
💡 Stay Emotionally Detached: Avoid being swayed by emotions like fear or greed. Stick to your investment strategy, even if the market experiences significant fluctuations.
💡 Consider Dollar-Cost Averaging (DCA): Instead of investing a lump sum, consider spreading your investment over time. This can help reduce the impact of market volatility.
💡 Stay Patient and Persistent: Long-term investing requires patience. Be prepared to hold through market ups and downs and avoid making impulsive decisions based on short-term events.
💡 Regularly Review Your Portfolio: Periodically assess your investments to ensure they align with your goals and risk tolerance. Make adjustments if necessary.
Remember, investing in cryptocurrencies carries inherent risks, and past performance does not indicate future results. Always invest an amount you can afford to lose, and consider consulting with a financial advisor if you’re unsure about any investment decision.
Best Long-Term Crypto Projects: Summary
When considering the best long-term crypto coins investments, thorough research is paramount. Understand the project, its team, and the technology.
Diversification is key, spread investments across different assets to mitigate risk. Exercise patience and avoid impulsive decisions. Stay updated with market trends and regulatory changes for informed choices.
FAQs About Best Long-Term Crypto
A long-term investment in cryptocurrency involves buying and holding digital assets with the expectation of profiting over an extended period, typically years.
They offer the chance for high returns, diversify your portfolio, and let you benefit from new technologies and growing industries.
Research the crypto’s purpose, team, and market potential. Be aware of the risks and volatility.
Established cryptocurrencies like Bitcoin and Ethereum are popular, but other promising projects like Cardano and Solana attract long-term investors.
Use reputable hardware wallets or secure software wallets. Avoid keeping large amounts on exchanges due to security risks.
Market trends, adoption rates, technological developments, regulatory changes, and the project’s ability to deliver on its promises.